In today’s interconnected world, cybersecurity is no longer a luxury but a critical necessity for modern businesses of all sizes. Cyber threats are constantly evolving, becoming more sophisticated and pervasive, posing significant risks to sensitive data, financial stability, and reputational integrity. Implementing essential cybersecurity practices is paramount to safeguarding your business from these ever-present dangers. This article will outline the essential cybersecurity practices that modern businesses must adopt to protect themselves from data breaches, ransomware attacks, phishing scams, and other malicious activities. Understanding and implementing these core security measures will significantly strengthen your defenses and mitigate the risks associated with operating in the digital age. From establishing robust security protocols to fostering a culture of security awareness, a proactive approach to cybersecurity is indispensable for long-term success.
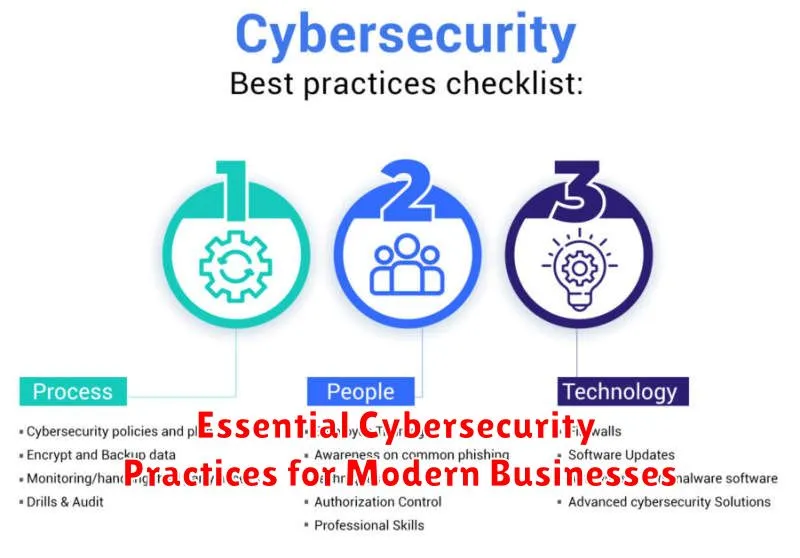
The following sections will delve into specific cybersecurity practices that are crucial for building a robust security posture. These practices encompass a range of areas, including network security, data protection, endpoint security, vulnerability management, incident response, and employee training. By addressing each of these key areas, businesses can create a comprehensive and layered cybersecurity strategy. This proactive approach will not only protect against immediate threats but also lay a strong foundation for future cybersecurity resilience in the face of evolving threats. Whether you’re a small startup or a large enterprise, implementing these essential cybersecurity practices is a fundamental investment in the future of your business.
Why Cybersecurity Matters Today
In today’s interconnected world, cybersecurity is no longer a luxury, but a necessity. Businesses of all sizes face an ever-evolving landscape of cyber threats, from sophisticated malware attacks to data breaches and ransomware.
The consequences of inadequate cybersecurity can be devastating. Financial losses due to stolen data, operational disruptions, and reputational damage can cripple a business. Moreover, failing to protect sensitive customer information can lead to legal and regulatory penalties.
Protecting digital assets, customer data, and intellectual property is paramount. A robust cybersecurity strategy is crucial for maintaining business continuity, building customer trust, and ensuring long-term success in the digital age.
Understanding Common Cyber Threats
Cyber threats are constantly evolving, making it crucial for businesses to understand the common risks they face. This awareness is the first step in implementing effective cybersecurity measures.
Some prevalent threats include:
- Phishing: Deceptive attempts to acquire sensitive information like usernames, passwords, and credit card details by masquerading as a trustworthy entity.
- Malware: Malicious software designed to damage or disable computer systems. Examples include viruses, ransomware, and spyware.
- Denial-of-Service (DoS) attacks: These attacks flood systems, servers, or networks with traffic to make them unavailable to users.
Understanding these and other cyber threats allows businesses to proactively address vulnerabilities and protect their valuable data.
Implementing Strong Password Policies
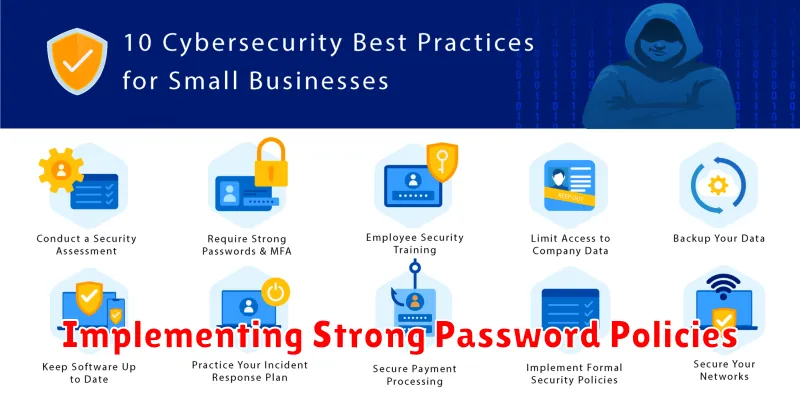
Strong password policies are fundamental to cybersecurity. They serve as the first line of defense against unauthorized access to sensitive business data.
Key elements of a robust password policy include:
- Password Length: Enforce a minimum password length, ideally 12 characters or more.
- Complexity Requirements: Mandate the inclusion of uppercase and lowercase letters, numbers, and symbols.
- Password History: Prevent users from reusing previously used passwords.
- Account Lockout: Implement account lockout mechanisms after a certain number of failed login attempts.
Regularly reviewing and updating your password policy is crucial to stay ahead of evolving cyber threats.
Using Multi-Factor Authentication
Multi-Factor Authentication (MFA) is a critical security measure that adds extra layers of protection beyond just a username and password. It requires users to provide two or more verification factors to access an account or system.
These factors typically fall into three categories:
- Something you know: A password, PIN, or security questions.
- Something you have: A security token, mobile phone, or smart card.
- Something you are: Biometric verification like fingerprint or facial recognition.
By requiring multiple factors, MFA makes it significantly more difficult for unauthorized individuals to gain access, even if they have compromised a password.
Implementing MFA across all systems and accounts, especially for privileged access, is essential for mitigating the risk of security breaches.
Regular Employee Cybersecurity Training
Consistent and comprehensive cybersecurity training is paramount for all employees. Human error remains a significant vulnerability, making regular training crucial for maintaining a strong security posture.
Training programs should cover topics such as:
- Password Management: Creating and maintaining strong, unique passwords.
- Phishing Awareness: Identifying and avoiding phishing attempts.
- Social Engineering: Recognizing and responding to social engineering tactics.
- Data Protection: Handling sensitive data securely.
- Device Security: Best practices for securing company devices.
Regular refreshers and updates on evolving threats are essential to keep employees informed and vigilant.
Securing Remote Work Environments
With the rise of remote work, securing these environments has become critical. Businesses must implement robust security measures to protect sensitive data accessed and transmitted by remote employees.
Key considerations include securing endpoints like laptops and mobile devices with strong passwords, multi-factor authentication, and up-to-date antivirus software. A secure Virtual Private Network (VPN) is essential for encrypting connections and protecting data transmitted over public networks.
Regular security awareness training for remote employees is vital. This training should cover topics like phishing scams, password management, and safe data handling practices. Implementing clear remote work security policies and procedures is also essential for maintaining a strong security posture.
Choosing the Right Security Software
Selecting appropriate security software is crucial for protecting your business. Prioritize solutions that address your specific needs and vulnerabilities. Consider the size of your business, the sensitivity of your data, and your budget.
Essential security software typically includes antivirus, firewall, intrusion detection/prevention systems (IDS/IPS), and data loss prevention (DLP) software.
Evaluate different vendors and their offerings. Look for reputable vendors with proven track records. Ensure the software is compatible with your existing systems and easy to manage.
Backup and Recovery Plans
A robust backup and recovery plan is essential for business continuity. Regular backups ensure data availability in case of system failures, cyberattacks, or accidental deletions. Critical data should be backed up frequently, with backups stored securely both on-site and off-site.
Recovery plans outline the steps to restore data and systems quickly and efficiently. These plans should be tested regularly to ensure their effectiveness and updated as systems evolve. Recovery time objectives (RTOs) and recovery point objectives (RPOs) should be defined to guide the recovery process.
Monitoring and Incident Response
Continuous monitoring of systems and networks is crucial for detecting suspicious activity. This includes analyzing logs, intrusion detection/prevention system alerts, and security information and event management (SIEM) data. Early detection can significantly minimize the impact of a security breach.
Having a well-defined incident response plan is essential. This plan should outline procedures for containing and eradicating threats, recovering systems, and conducting post-incident analysis to prevent future occurrences. Regularly testing and updating this plan is vital for its effectiveness.
Staying Ahead with Security Updates

In today’s rapidly evolving threat landscape, staying ahead with security updates is paramount. Software vulnerabilities are constantly being discovered, and cybercriminals are quick to exploit them. Regularly updating your software is one of the most effective ways to mitigate these risks.
This includes operating systems, applications, firmware, and any other software running on your network. Automated updates are highly recommended whenever possible to ensure timely patching. Manual updates should be performed promptly when automation isn’t feasible.
Prioritize updates for critical systems and those facing direct internet exposure. Establish a clear update management process, including testing updates in a non-production environment before deployment to avoid potential compatibility issues.